In Windows Server and Windows 11, users are assigned administrative ability through group membership. Typically, built-in groups are used to support this process. For example, to enable a user to perform server management tasks, you can add their user account to the Server Operators local group. Because the Server Operators local group has been automatically assigned numerous management abilities, a user added to that group inherits the abilities of that group. This process is referred to as group-based security.
In Intune, a different process is used; this process is called role-based access control. Although you can use RBAC to assign management and administrative permissions in Intune, RBAC is usually managed in Azure AD. Although your job function might not entail configuring RBAC in Azure AD, it’s probably worth reviewing some of the available settings.
Configuring RBAC in Azure AD
There are numerous built-in roles in Azure AD. You can rely solely on these roles and, for many situations, they’ll provide you with the necessary management delegation you likely need. However, you can also create custom roles; these are roles for which you define the management permissions to suit your specific organizational requirements.
You use the Microsoft Entra admin center or the Azure Active Directory admin center to manage and assign roles.
Note Microsoft Entra or Azure Active Directory Admin Center
You can use either of these management consoles to perform Azure AD management and administration tasks. However, because Microsoft Entra is the newer administrative console, we focus on that throughout this book.
In Microsoft Entra, expand Azure Active Directory in the navigation pane, then expand Roles & admins. Select the Roles & admins node, as displayed in Figure 2-7.
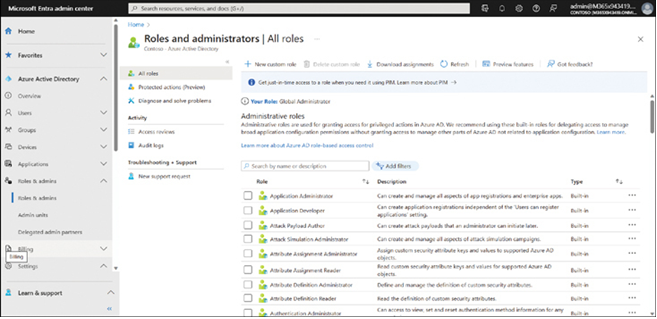
FIGURE 2-7 Reviewing RBAC roles in Microsoft Entra
You can search for a specific role and then review who has that role assigned. For example, in the search box, enter Intune and then select the Intune Administrator role from the returned list.
On the Assignments tab, you can review and modify role-holders. To add an assignment, use the following procedure:
- Click Add assignments.
- Click the No member selected link.
- In the Select a member pane, select a user or group to which you want to assign the role. Click Next.
- You can now choose between the following options:
• Eligible Means that the user can exercise the permissions of the assigned role. You can then make the assignment permanently eligible or define a time range. When a user is eligible for a role, a designated administrator must confirm their use of that role when the user attempts to exercise their administrative permissions.
• Active Means the user can immediately exercise the administrative permissions associated with the assigned role.
Note Privileged Identity Management
The choice between Eligible and Active is only possible when “Privileged Identity Management (PIM)” is activated in the Azure subscription.
- Click Assign.
Note Assign Roles to Groups
It’s best practice to assign a role to a group—even if it contains only one user. This is because it makes ongoing administration easier. For example, if the Azure AD security group Contoso Device Admins contains a user called AndrewW, and you have assigned the Intune Administrator role to Contoso Device Admins, AndrewW has that through their group membership. To remove that role from AndrewW, you merely need to remove AndrewW from the Contoso Device Admins group. You might then add SallyM to the Contoso Device Admins group, thereby assigning the Intune Administrator role to SallyM. It’s important that when you create groups you intend to use in this way, you remember to enable the Azure AD roles can be assigned to the group option.
When you assign a role, you can assign it to the entire directory (which means everything in your Azure AD tenant), or you can use Admin units. These are similar to organizational units (OUs) in an on-premises AD DS infrastructure, allowing for a more targeted delegation of admin permissions.
You define the scope of the role when you add a user or group to the role. That’s to say, you select the Scope type option on the Add assignments page, as displayed in Figure 2-8. You can then select either Directory (the default) or Administrative unit. You must then choose the appropriate admin unit.
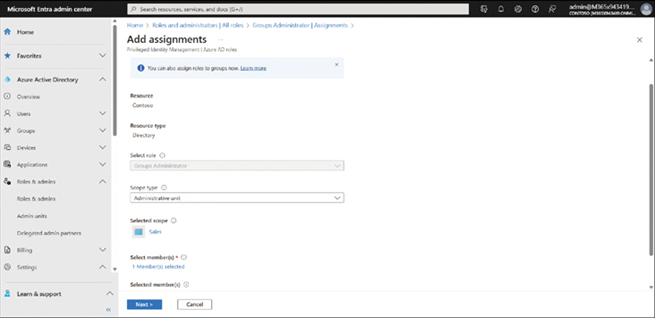
FIGURE 2-8 Scoping the application of a role
As an Endpoint Administrator, your job role entails performing device management and related tasks. In Azure AD, there are a number of relevant RBAC roles for administrative tasks in Microsoft Intune. These are:
- Intune Administrator Role holders can manage all aspects of Microsoft Intune.
- Azure AD Joined Local Administrator Users assigned to this role are added to the local administrators group on Azure AD-joined devices.
- Cloud Device Administrator Users with this role have limited device management capabilities, including enabling, disabling, and deleting devices.

