Device management requires configuration to ensure that when your users attempt device registration (register or join), the process doesn’t fail. By default, the setting is enabled, allowing all Windows 11 devices with valid credentials to be managed by your Azure AD.
Typically, you’ll use Microsoft Entra to configure the required settings. Use the following procedure to verify and, where necessary, update the settings:
- Open the Microsoft Entra admin center.
- Under Azure Active Directory in the navigation pane, select Devices, and then click Overview.
- On the Devices | Overview page, click Device settings.
- As shown in Figure 2-10, enable the Users may join devices to Azure AD setting. You can choose All to allow all users to perform this task, or you can choose Selected and choose which users can perform this task.
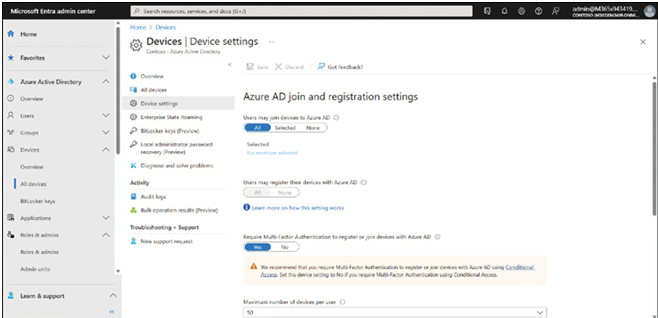
FIGURE 2-10 Configuring the settings for Azure AD registration or join
- If necessary, also enable Users may register their devices with Azure AD.
- Enable the Require Multi-Factor Authentication to register or join devices with Azure AD setting for additional security. However, you must ensure that users’ accounts are configured with the necessary settings for MFA.
- Finally, click the Manage Additional local administrators on all Azure AD joined devices link to add specified users as local administrators on joined devices. Any users you add are assigned to the Azure AD Joined Device Local Administrator role. This setting ensures that a cloud user is always added as a local admin on all your organization’s devices.
- You can also enable the Azure AD Local Administrator Password Solution (LAPS) setting for any new devices.
On the Device settings page, you can fine-tune the process of registering and joining devices by configuring the device settings, as shown in Table 2-1.
TABLE 2-1 Azure AD device configuration settings
| Device setting | Description |
| Users May Join Devices To Azure AD | Allows you to select users that can join Windows 11 devices to Azure AD. The default is All. |
| Users May Register Their Devices With Azure AD | Allows devices to be registered with Azure AD by users. Options include: None: Prevents devices from being registered with Azure AD.ALL: Automatically configured if Enrollment with Microsoft Intune or Mobile Device Management (MDM) for Office 365 is configured as they require Device Registration. |
| Require Multi-Factor Authentication To Register Or Join Devices With Azure AD | Determines whether users are required to use multifactor authentication factor to join their devices to Azure AD. This setting only applies to Azure AD Join on Windows 11 and BYOD registration for Windows 11, iOS, and Android. This setting does not apply to hybrid Azure AD–joined devices, Azure AD–joined VMs in Azure, and Azure AD–joined devices using Windows Autopilot self-deployment mode. The default setting is No. |
| Maximum Number Of Devices Per User | Restricts the number of devices per user. Once this quota is reached, they cannot add devices until one or more existing devices are removed. The device quota is across both Azure AD–joined and Azure AD–registered devices. By default, all users can have a maximum of 50 devices in Azure AD. |
| Manage Additional Local Administrators On All Azure AD Joined Devices | Enables you to assign the users that are granted local administrator rights on a device and added to the Device Administrators role in Azure AD. By default, global administrators in Azure AD and device owners are granted local administrator rights. Requires an Azure AD Premium license. |
| Enable Azure AD Local Administrator Password Solution (LAPS) | Helps you securely manage the passwords of local accounts on joined devices. Defaults to No. This is discussed in more detail later in this chapter. |
| Restrict Users From Recovering The BitLocker Key(s) For Their Owned Devices | Determines if users can recover their BitLocker key(s). If enabled, the setting restricts non-admins from being able to access the BitLocker key(s) for their own devices. Selecting No enables users to recover their BitLocker key(s). Defaults to No. |
Connect devices to Azure AD
Once the prerequisites have been configured to allow device registration service to take place, you can connect devices to Azure AD.
There are three ways to connect a Windows 11 device to Azure AD as follows:
- Join a new Windows 11 device to Azure AD
- Join an existing Windows 11 device to Azure AD
- Register devices to Azure AD
In this section, you’ll learn the steps required to connect Windows 11 to Azure AD.

